In the period from February to August 2019 Digital Security Lab Ukraine registered 48 different security incidents.
Methodology
Digital Security Lab Ukraine register digital security incidents that happen with non-profit organizations, activists and media. For our monitoring, we use the information directly from organizations and activists that used our helpline, but also from open sources, mostly news and social media. Also, we note if the target is investigative journalist/organization, anti-corruption activist/organization, related with Crimea or Donbas region, or LGBT.
Our taxonomy for types of incidents includes three major groups: incidents with accounts, incidents with devices and incidents with websites. “Devices” have subtypes: received (in email, via messenger etc) targeted malware, received untargeted malware, malware detected on device, seizure of devices, device stolen or lost, data loss due to malfunction, devices check on border, LAN intrusion. “Websites” have subtypes: DDoS, other website attack. “Accounts” have: targeted phishing, untargeted phishing, account takeover, account takeover attempt, account lockout.
Account-related incidents (27)
21 attempts of account takeovers twelve of them were it was a successful one. In 8 cases Digital Security Lab were able to provide some kind support, including successful account control recovery.
In at least seven of those cases attackers were using some kind of phone number takeover to either get control over Telegram and/or Whatsapp accounts, or use it in account recovery process in email account.
In at least four cases enabled 2FA stopped attackers from account takeover. In other two publicly reported incidents of the account takeover victims claimed that they had some form of 2FA enabled, but we weren’t able to confirm those claims ourselves or otherwise investigate root of the account compromise.
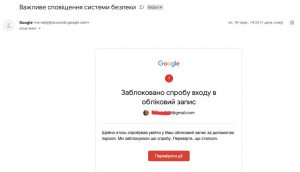
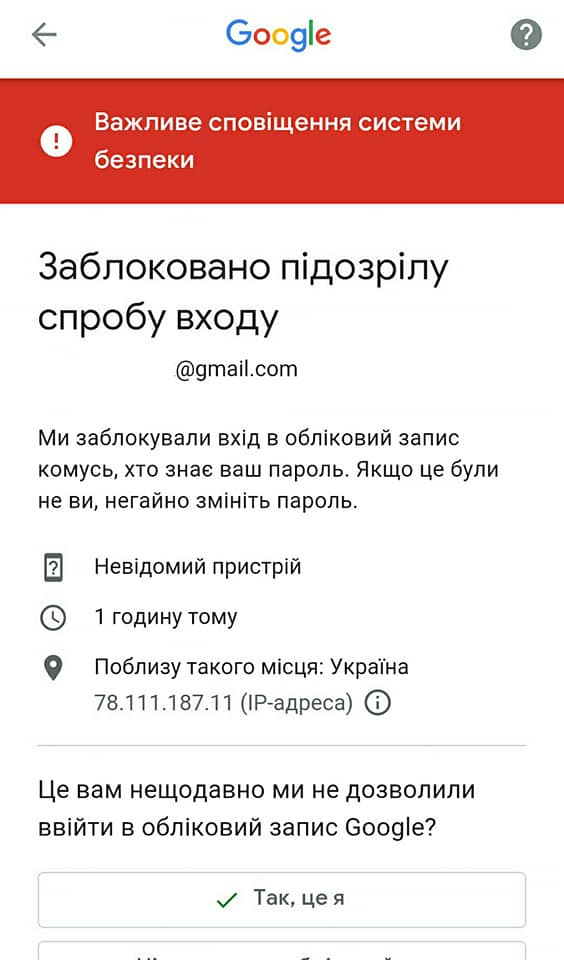
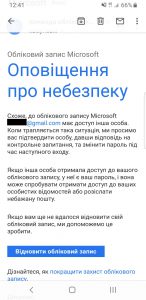
We registered only three cases of complete account lockout – without the ability to regain control over lost account. But such a low number may be rather a sign of an underreporting due to a victim feeling that’s it his own fault, than indicator of actual number of incidents.
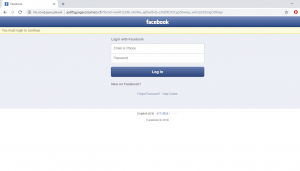
Phishing (4)
We got four cases of a targeted phishing during this period, of them three being focused on Facebook, and two being cases of similar attacks against public pages of different CSOs active in Ukraine.
Website-related incidents (1)
We have counted at least one case of a DDoS attack against TV and radio station website and infrastructure, due to which there was a disruption in the station’s airing.
Device-related incidents (15)
Also, we’ve seen a number of incidents involving physical access to devices or premises, but it is, as expected, a bit lower than remote attacks against accounts.
In three cases journalist’s devices were stolen or taken. In one of them a video operator was directly attacked and memory card with the filmed material was taken. Another journalist was also attacked and his mobile phone was taken and destroyed.
We registered nine cases of break-in or warranted search. In two cases, devices were seized by Ukrainian police as “an evidence in criminal investigation”.
Another case was a break-in into the former office of the investigation journalist team, but the reported target was paper documents, not electronic devices. There was an attempt of break-in into the office of another investigative journalist team editorial office. Five others searches and device seizures were conducted by Russian security in occupied Crimea.
One quite significant incident involved loss of sensitive data due to a physical malfunction of the hard disk where it was stored. Organisation was advised against going to local data-recovery companies, due to their tight connections to law enforcement and subsequent high risk of data leakage.
We confirmed at least one case of the device search during the entering into the Russian-occupied Crimean peninsula. Journalist was told to show photo she has on her phone and its IMEI was recorded as well. In a similar case, involving activist going to Crimea, Russian officials also recorded person’s phone IMEI.
Targets
Thirteen incidents happens to investigative journalists, most of them being attempted or successful account takeovers.
Seven incidents involved journalists and activists in occupied Crimea or associated with it.
Two cases involved members of LGBTQ community.